Dieser Blog Aggregator enthält sowohl die aktuellen Meldungen aus unserem offiziellen Blog als auch meinen persönlichen Blog mit technischen Beiträgen rund um Open Source und Freie Software.
A short status update of what happened on my side last month. Was able to test our Cellbroadcast bits, feedbackd became more flexible regarding LEDs, Phosh 0.40 is out, and some more.
Phosh
- Phosh 0.40.0
- Fix testing custom quick setting plugins (MR)
- Add icons for dark style toggles (thanks to Sam Hewitt for the help) (MR, MR)
- 0.39.x backports (MR)
- Set default sound-theme (MR)
- Launch apps in transient scope (MR)
- Allow to suspend from lock screen (MR)
- Fix media player button style (MR)
- Don't use plain .so for bindings lib (MR)
Phoc
- Fling gesture to open/close phosh's panels (MR)
- Fix crash on output removal (MR)
- Don't draw decorations when maximized (MR)
- Allow to stack layer surfaces (MR was a bit older, polished up to land it) (MR)
gmobile
- Add hwdb support for Juno tablets (based on information by Giovanni Caligaris) (MR)
- Support add generic BT AVRCP profile (with the help of Phil Hands) (MR)
- Released 0.2.1
phosh-mobile-settings
- Use shared gmobile (MR)
phosh-wallpapers
- Add sound theme (MR)
emacs
- Add a major mode for systemd-hwdb files (MR)
Debian
- Backport phog fix to work with phosh-osk-stub (MR)
- Release git snapshot of phosh-wallpaper for NEW processing (MR)
- Backport phosh fixes for 0.39.0 (MR)
- Phoc: Install examples, they're useful for debugging (MR)
- Make libpam-ccreds work with gcrypt 1.11:
- Upload phosh release 0.40.0~rc1 and 0.40.0
- phog: Add example for autologin (MR)
- Update firefox-esr-mobile-config (thanks to Peter Mack for the input) (MR)
- Tweak meta-phosh:
ModemManager
- Test our current code at NLalert test day: Current branch
Feedbackd
- Only apply Qualcom bits to lpg driver (MR)
- Support arbitrary RGB values for multicolor LEDs (MR)
- Allow to use camera flash LEDs as status LEDs (MR)
- End too noisy feedback when switching profile levels (MR)
- Packaging fixes (MR) , MR)
- device-themes: Lower brightness of feedback events as the flash is too bright on OnePlus 6T (MR)
- cli: Inform user when nothing was triggered (MR)
- Released 0.4.0
Livi
Calls
Chatty
- Allow to display a Matrix clients access token (MR)
- libcmatrix: Add support handling push notification servers (MR)
- Allow to add push notification servers (draft)) (MR)
- Package docs (MR)
meta-phosh
Libhandy
- Fix use-after-free in stackable-box (MR)
If you want to support my work see donations.
A short status update of what happened on my side last month. A broken gcovr in Debian triggered a bit of busy work but 0.39.0 came out nicely nevertheless. We also reduced build time quiet a bit in phosh and phoc.
Phosh.mobi
- Release Phosh 0.39.0
- Blog post on wakeup keys
- Start video section
phosh
- Split mocked and real wall clock: Merge request
- Speed up build: Merge request
- Update CI and fix some leaks: Merge request
- Generate initial Rust bindings for libphosh: https://gitlab.gnome.org/guidog/libphosh-rs
- Preps for that:
- Split headers from sources: Merge request
- Allow to install headers and shared object: Merge request
- Preps for that:
- Wire up screenshot keybinding: Merge request
- Expose
OverviewActiveproperty: Merge request - Further reduce build time: Merge request
- Add mocks for ModemManager and NM data connections: Merge request
phoc
- Move udev rules and hwdb entries downstream: Merge request
- Speed up build: Merge request
- Update wlroots to 0.17.3: Merge request
- Doc updates: Merge request
gmobile
- Add wakeup-key hwdb and udev rules: Merge request
- Release 0.2.0: Merge request
- Simplify testing panel information of different devices: Merge request
- Add hwdb entries for more devices: Merge request
calls
- Update ci images so MRs using newer libadwaita can land: Merge request
mobile-broadband-provider-info:
feedbackd
- Initial libfeedback Rust bindings
- Test led probing using umockdev: Merge request
livi:
- Update flatpak deps: Merge request (This includes a patch from Sebastian Dröge to optionally switch to gtk4paintable sink)
- Add GSetting for auido visualizer: Merge request
chatty / libcmatrix
- Update libcmatrix. This pulls in our changes from last month.
python-dbusmock
- Add initial ModemManager mock: Merge request (Makes the ModemManager mock in Phosh mentioned above simpler)
Linux kernel
- Export wakeup keys: Merge request
- Don't wake up on volume key press: Merge request
libcall-ui
- Release 0.1.2: Merge request
Debian
- Fix and upload gcovr: Merge request, Issue
- Workarond gcovr breackage in phosh-osk-stub, gmobile, mobile settings and phosh
- Update wlroots
- Upload 0.17.2 to sid: Merge request
- Upload 0.17.3 to exerimental: Merge request
- Mobile tweaks:
- Upload new version: Merge request
- Cleanup a bit: Merge request
- update Librem 5 power mgmt rules so we don't lose the modem: Merge request (allowed me to drop all PureOS packages on my cross graded device)
- feedbackd: Install missing docs (Closes: #1050601): Merge request
If you want to support my work see donations.
A short status update of what happened on my side last month. Maintenance and code review keep to be the top time sinks (in a positive way).
phosh: A Wayland shell for mobile devices
- Release phosh 0.37.1
- Release phosh 0.38.0
- Be more generous in the gnome-session versions we support: Merge Request
- Improve notification timestamps for translations: Merge Request
- Improve test coverage a bit: Merge Request
- Improve introspection data and documentation (Merge Request 1, Merge Request 2). Besides better docs (we now also fail on new warnings and errors (Merge Request) this allows to use parts of phosh in e.g. display managers in languages using introspection (Rust, JS, …). See this issue how this could become useful.
- Add night light quick settings toggle: Merge Request
- Fix power menu rendering without Cantarell: Merge Request
- Track settings state (Merge Request) in shell state flags too. This will be useful to make tests more robust.
phoc: A wlroots based Wayland compositor mostly used on mobile phones
- More internal cleanup: Merge Request
- Use shared gmobile: Merge Request
- More introspection fixes to improve doc builds: Merge Request
- Fix window cycle order: Merge Request
- Fix crash with cutout/notch debug: Merge Request
phosh-tour: A short introduction to Phosh
- Fix blurry images: Merge Request
- Fix flatpak build: Merge Request
- Fix packaging build: Merge Request
- Add a small Getting started page so phosh-tour has anything to point at
gmobile: Functions useful in mobile related, glib based projects
- Release 0.1.0
- Update docs for shared lib use: Merge Request
- Upload to Debian: https://packages.debian.org/sid/libgmobile0
libcall-ui: Common user interface parts for call handling
- Release 0.2.0: Merge Request
calls: Phone calls application
- Fix crash without location services: Merge Request
phosh-ev: Monitor battery status of an electric car
- Switch flatpak runtime to GNOME 46: Merge Request
phosh-mobile-settings: Mobile specific settings
- osk: Allow to configure whether to ignore hardware keyboards: Merge Request
- Fix build without phoc: Merge Request
- Allow to organise additional quick settings: Merge Request
epiphany Don't make it appear frozen on first start: Merge Request
iio-sensor-proxy (missed that one in March): Make test-suite more robust so people aren't puzzled when trying things locally: Merge Request
mobile-broadband-provider-info Prepare Release: Merge Request
feedbackd: A daemon to provide haptic, led and audio feedback triggered by application events
- Allow to override feedback level: Merge Request (gnome-clocks branch using this)
- Allow to use shared gmobile: Merge Request
- Release 0.3.0: Merge Request
meta-phosh Update dependency set: Merge Request Use common style check: Merge Request
phosh nightly: Package builds of current Phosh git
- Add some more packages that are useful for mobile: https://source.puri.sm/guido.gunther/phosh-debs
livi: A small video player targeting mobile devices
- Add devel profile to ease having the devel and release flatpak installed: Merge Request
chatty / libcmatrix: Assorted fixes. Some to make matrix a bit more robust:
- Don't forget to call sync callback: Merge Request
- Improve copy popover: Merge Request
- Drop support for libsoup2: Merge Request
- Matrix robustness: Merge Request
- Fix Matrix image download: Merge Request
- Fix Doc build and make sure more methods end up there: Merge Request
systemd:
- Discuss hwdb and udev rules so we can track unidle/wakup keys: hwdb Merge Request, udev Merge Request to better handle device tree devices. As it turns out we'll do most of this in phoc initially and then open another merge request once we have more data.
librem5-flash-image
- Bring it back to debian testing: https://tracker.debian.org/pkg/librem5-flash-image
If you want to support my work see donations.
A short status update of what happened on my side last month. I spent quiet a bit of time reviewing new, code (thanks!) as well as maintenance to keep things going but we also have some improvements:
Phosh
- Release phosh 0.37.0
- Add support for progress indicator and counts to lockscreen launcher entries: Merge request, Demo using Phosh-EV's charge status as example (Merge request)
- Fix 5G with MM: Merge Request
- Doc updates: Merge Request
- Drop builtin session support Merge request
- Support gnome-session 45/46: Merge request
- Add plymouth theme: Merge Request
- OSD improvements: Merge Request
- Monitor: Only use
wl_output_doneand background fixes: Merge Request - Support phones with rounded display corners: Merge Request
- CI maintenance: Merge Request
Phoc
- More fractional scale fixes: Merge Request
- Dedup pointer constrain code: Merge Request
- xdg-shell: Check serial on move/resize: Merge Request
- Add an animation when toggling always on top: Merge Request
- Make ViewChild a GObject: Merge Request
- Validate more things during build: Merge Request
- Update to wlroots 0.17.2: Merge Request
phosh-mobile-settings
- CI maintenance: Merge Request
phosh-osk-stub
- Detect and optionally disable when hardware keyboard is present: Merge Request
- Coloring fixes for HighContrast: Merge Request
- CI maintenance: Merge Request
gmobile
- Make a shared library: Merge Request
- Let it work with recent json-glib : Merge Request
Livi
- Allow to preprocess pasted URLs: Merge request
- Bump GTK dependency and add fallback so we can land Robert's GtkOffload support: Merge request
- Allow to list recent videos: Merge request
- Check for Wayland support early: Merge Request
squeekboard
- Build against newer dependencies: Merge Request
- Forward to glib 2-58: Merge Request
- CI maintenance: Merge Request
GNOME calls
- Release 46.0: Merge Request
Libsoup
- Don't export too many symbols: Merge Request
If you want to support my work see donations.
A short status update what happened last month. Work in progress is marked as WiP:
GNOME Calls
- Landed support to pick emergency calls numbers based on location (until now Calls picked the numbers from the SIM card only): Merge Request
- Bugfix: Fix dial back - the action mistakenly got disabled in some circumstances: Merge Request, Issue.
Phosh and Phoc
As this often overlaps I've put them in a common section:
- Prepare and release Phosh 0.36.0 and upload to Debian
- phoc: Implement always on top and allow to move to corners via keybindings: Merge Request, Demo
- phoc: Wire up support for fractional-scale-v1 protocol: Merge Request. Issue
- phoc: Go with the flow and don't use APIs that will be removed in wlroots 0.18, thus switch to render pass: Merge Request
- phoc (as art of my ongoing cleanups to make the code base more approachable):
- Make PhocServer private: Merge Request
- Move drag-icon handling into it's own file: Merge Request
- phosh: load backgrounds asynd and handle dark theme URIs: Merge Request
- WiP: Allow to use wallpapers in lock screen and overview: Merge Request 1, Merge Request 2, Merge Request 3
- phosh: Add a caffeine quick-setting: Merge Request, Demo
- phosh and phoc bug fixes
- Fix Maximized map of X11 surfaces: Merge Request
- vpn fix: Merge Request
- Fix crash around emergency calls: Merge Request
- Honor disabled locking when there's no lock delay: Merge Request
- Testsuite improvements:
- Speedup tests: Merge Request
- Load plugins in tests: Merge Request
- release gmobile 0.0.6
Phosh Tour
- Allow for hardware specific pages: Merge Request
- Catch up with library and CI improvements: Merge Request
Phosh Mobile Settings
- Filter lockscreen plugins on lockscreen page: Merge Request
Phosh OSK Stub
- Add OSK side workaround for splash timeouts until GTK side is merged: Merge Request
- Update emoji data: Merge Request
Livi Video Player
- Remember stream position: Merge Request
- Label SDH subtitles: Merge Request
- Show controls when window becomes active: Merge Request
Phosh.mobi Website
- Directly link to tarballs from the release page, e.g. here
If you want to support my work see donations.
As the ecosystem around phosh continues to grow it can become harder for distributions and users to keep track of what actually makes up Phosh and what the current versions are. So let's spell out components and dependencies replacing the social media only announcements. The list is generated from the individual projects NEWS files and this was a good opportunity to automate the release process further. It looks like this now.
Edit (on 2023-03-09): Replaced the actual 0.24.0 release notes by a link to avoid confusion about the canonical location.
I wanted to look back at what changed in phosh in 2022 and figured I could share it with you. I'll be focusing on things very close to the mobile shell, for a broader overview see Evangelos upcoming FOSDEM talk.
Some numbers
We're usually aiming for a phosh release at the end of each month. In 2022 We did 10 releases like that, 7 major releases (bumping the middle version number) and three betas. We skipped the April and November releases. We also did one bug fix relesae out of line (bumping the last bit of the version number). I hope we can keep that cadence in 2023 as it allows us to get changes to users in a timely fashion (thus closing usability gaps as early as possible) as well as giving distributions a way to plan ahead. Ideally we'd not skip any release but sometimes real life just interferes.
Those releases contain code contributions from about 20 different people and translations from about 30 translators. These numbers are roughly the same as 2021 which is great. Thanks everyone!
In phosh's git repository we had a bit over 730 non-merge commits (roughly 2 per day), which is about 10% less than in 2021. Looking closer this is easily compensated by commits to phoc (which needed quite some work for the gestures) and phosh-mobile-settings which didn't exist in 2021.
User visible features
Most notable new features are likely the swipe gestures for top and bottom bar, the possibility to use the quick settings on the lock screen as well as the style refresh driven by Sam Hewitt that e.g. touched the modal dialogs (but also sliders, dialpads, etc):
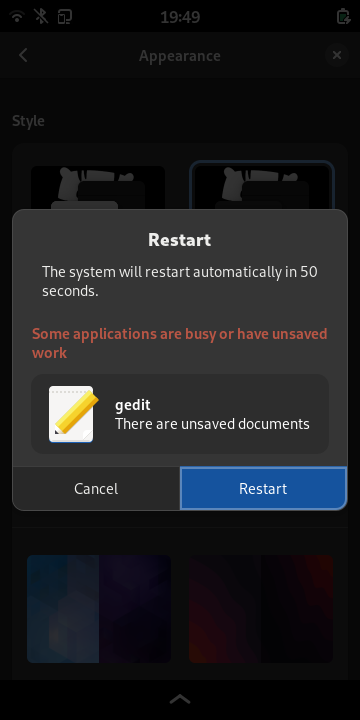

We also added the possibility to have custom widgets via loadable plugins on the lock screen so the user can decide which information should be available. We currently ship plugins to show
- information on upcoming calendar events
- emergency contact information
- PDFs like bus or train tickets
- the current month (as hello world like plugin to get started)
These are maintained within phosh's source tree although out of tree plugins should be doable too.
There's a settings application (the above mentioned phosh-mobile-settings) to enable these. It also allows those plugins to have individual preferences:
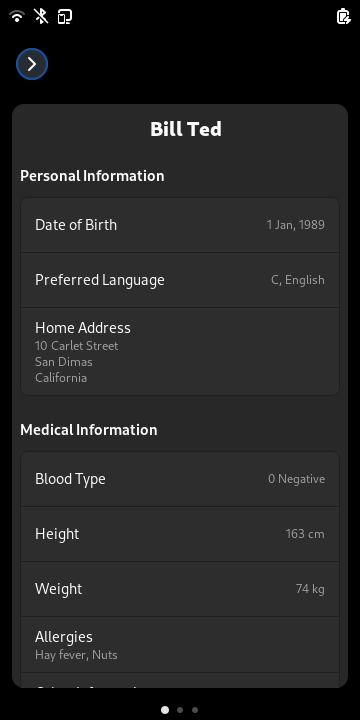
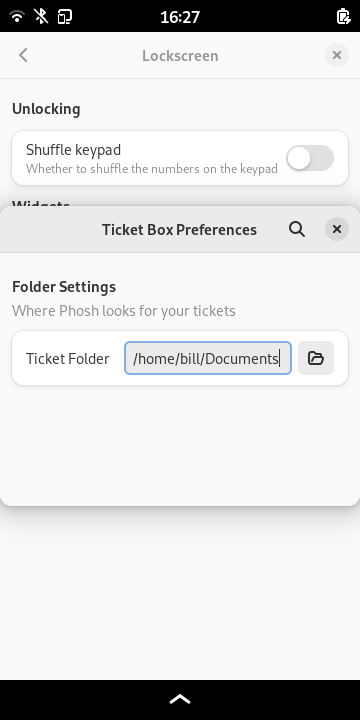
Speaking of configurability: Scale-to-fit settings (to work around applications that don't fit the screen) and haptic/led feedback are now configurable without resorting to the command line:
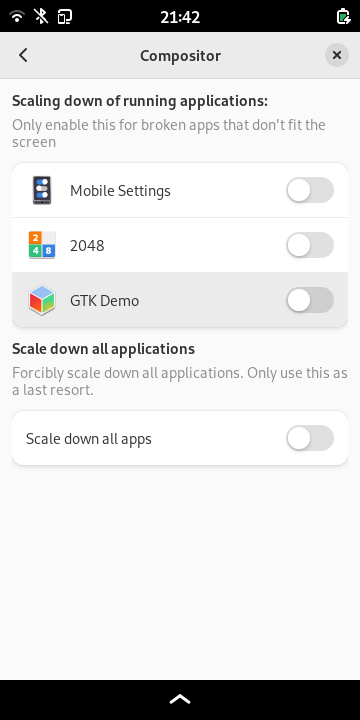
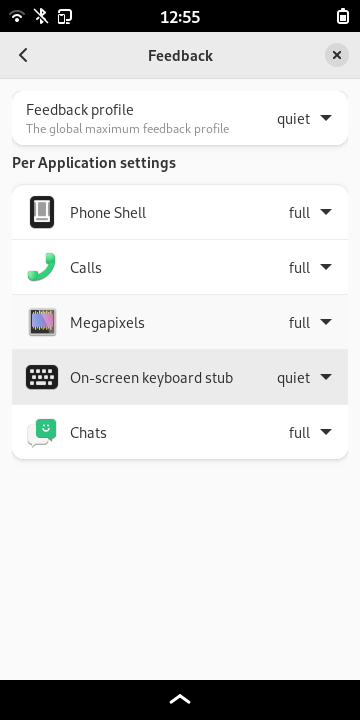
We can also have device specific settings which helps to temporarily accumulate special workaround without affecting other phones.
Other user visible features include the ability to shuffle the digits on the lockscreen's keypad, a VPN quick settings, improved screenshot support and automatic high contrast theme switching when in bright sunlight (based on ambient sensor readings) as shown here.
As mentioned above Evangelos will talk at FOSDEM 2023 about the broader ecosystem improvements including GNOME, GTK, wlroots, phoc, feedbackd, ModemManager, mmsd, NetworkManager and many others without phosh wouldn't be possible.
What else
As I wanted a T-shirt for Debconf 2022 in Prizren so I created a logo heavily inspired by those cute tiger images you often see in Southeast Asia. Based on that I also made a first batch of stickers mostly distributed at FrOSCon 2022:

That's it for 2022. If you want to get involved into phosh testing, development or documentation then just drop by in the matrix room.
The Librem 5 features a built-in smartcard reader. While most people use it for gpg I wanted to see if it can be used as an authenticator for services like email (SMTP, IMAP), access to web pages (HTTPS), calendars, etc without either having to retype a password often or having to store it on the device itself: single sign on for all my frequently used services.

For that one can leverage a feature called PKINIT of Kerberos (a network authentication protocol meant to allow secure communication over a non-secure network) which uses public key cryptography for initial user authentication (instead of a password). If the key material is saved on the smart card even a lost device can hardly be abused as the smart card is protected by a PIN and will lock itself after three incorrect tries (and you can easily revoke the certificate server side too).
On the service side one can use SASL/GSSAPI to make services like exim, postfix, dovecot, cyrus imapd, apache, nginx or prosodi use Kerberos to authenticate users and there's many more (like CalDAV servers, etc). The most prominent missing bit for me is currently the Synapse matrix server not supporting GSSAPI yet.
I won't go into the details of setting up the Kerberos server (KDC) or PKINIT itself or how to configure services as this is already done elsewhwere (1, 2) but rather focus on the Librem 5 and smart card side.
So for the following let's assume you have a Kerberos realm called
MS20.NIX set up and your KDC has the DNS name kdc.ms20.nix, and
your Kerberos principal (your user in the Kerberos database) is called
foo@MS20.NIX. You also have an smtp and imap servers called
smtp.ms20.nix and imap.ms20.nix set up to autenticate users via
Kerberos. Finally we call the CA that signs all your certificates
ca.pem (were're following the naming from 2).
What follows looks as if lots of things need to be done on the command line. I'll show a simplification at the very end but wanted those bits written down for reference/debugging. Note that this post is not meant as an exhaustive introduction but more like a quick summary of commands. I'm happy if someone grabs it and adds more details.
Kerberos Setup on the Librem 5
Let's first install the Kerberos client side packages on the phone and test that:
$ sudo apt install heimdal-clienets
The krb5-config package will ask for your Kerberos realm, KDC etc. With that in place
you should be able to test if you can get a Kerberos ticket via
$ kinit
and entering your password.
If that worked the klist output will look something like:
$ klist
Ticket cache: FILE:/tmp/krb5cc_1000
Default principal: foo@MS20.NIX
Issued Expires Principal
Oct 24 12:55:13 2022 Oct 25 12:55:13 2022 krbtgt/MS20.NIX@MS20.NIX
Now that basic authentication worked We're ready to switch to certificates stored them on the smart card. Let's drop the credentials first:
$ kdestroy
Smartcard Setup
I have used an OpenPGP card smartcard and inserted that into the Librem 5. In my case it was salvaged from a Librem Key. As PKINIT uses OpenSC the OpenSC wiki was very helpful as it has details on how to get key material onto that particular card.
The software to use the Librem 5's smart card reader is enabled by default as part of the librem5-base package. You just need to add opensc to the mix:
$ sudo apt install opensc
With that you should already be able to see the card:
$ opensc-tool -l
# Detected readers (pcsc)
Nr. Card Features Name
0 Yes L5 built-in SmartCard Reader 00 01 00 00
1 Yes L5 built-in SmartCard Reader 00 01 00 01
As there's only a single reader and the second entry can confuse opensc let's ignore that one:
$ cat <<EOF > /etc/opensc/opensc.conf
app default {
ignored_readers = "TTXS serial 00 01 00 01","L5 built-in SmartCard Reader 00 01 00 01"
}
EOF
Which should make the output look like
$ opensc-tool -l
# Detected readers (pcsc)
Nr. Card Features Name
0 Yes L5 built-in SmartCard Reader 00 01 00 00
With the reader up and running we can now store the certificate and private key on it. For simplicity we create these on the KDC and transfer them to the phone (a more realistic setup would create those locally and use a certificate signing request so the private key never leaves your hands):
On the KDC:
$ hxtool issue-certificate --ca-certificate=FILE:krbca.pem --generate-key=rsa --key-bits=2048 --type="pkinit-client" --pk-init-principal="foo@MS20.NIX" --subject="uid=foo,DC=ms20,DC=nix" --certificate="FILE:user.pem"
Then you'd copy the file to your phone and install certificate and private key on the smartcard like (this will delete any already existing keys on the card):
$ # Install needed packages
$ sudo apt install opensc wipe
$ # Delete old keys and install certificate and private key on smartcard
$ pkcs15-init --delete-objects privkey,pubkey,cert --id 1 --auth-id 3
$ pkcs15-init --delete-objects privkey,pubkey,cert --id 2 --auth-id 3
$ pkcs15-init --delete-objects privkey,pubkey,cert --id 3 --store-private-key user.pem --store-certificate user.pem --id 3 --auth-id 3
$ # Wipe the file containing the private key
$ wipe user.pem
Afterward we can look at what's on the card
$ pkcs15-tool -D
Using reader with a card: L5 built-in SmartCard Reader 00 01 00 00
PKCS#15 Card [OpenPGP card]:
Version : 0
Serial number : <serial number>
Manufacturer ID: ZeitControl
Language : de
Flags : PRN generation, EID compliant
PIN [User PIN]
Object Flags : [0x03], private, modifiable
Auth ID : 03
ID : 02
Flags : [0x13], case-sensitive, local, initialized
Length : min_len:6, max_len:64, stored_len:64
Pad char : 0x00
Reference : 2 (0x02)
Type : UTF-8
Path : 3f00
Tries left : 3
PIN [User PIN (sig)]
Object Flags : [0x03], private, modifiable
Auth ID : 03
ID : 01
Flags : [0x13], case-sensitive, local, initialized
Length : min_len:6, max_len:64, stored_len:64
Pad char : 0x00
Reference : 1 (0x01)
Type : UTF-8
Path : 3f00
Tries left : 3
PIN [Admin PIN]
Object Flags : [0x03], private, modifiable
ID : 03
Flags : [0x9B], case-sensitive, local, unblock-disabled, initialized, soPin
Length : min_len:8, max_len:64, stored_len:64
Pad char : 0x00
Reference : 3 (0x03)
Type : UTF-8
Path : 3f00
Tries left : 3
Private RSA Key [Authentication key]
Object Flags : [0x03], private, modifiable
Usage : [0x222], decrypt, unwrap, nonRepudiation
Access Flags : [0x1D], sensitive, alwaysSensitive, neverExtract, local
Algo_refs : 0
ModLength : 2048
Key ref : 2 (0x02)
Native : yes
Auth ID : 02
ID : 03
MD:guid : 135c302c-ddad-1a3c-f558-8beae7612f9f
Public RSA Key [Authentication key]
Object Flags : [0x02], modifiable
Usage : [0x51], encrypt, wrap, verify
Access Flags : [0x02], extract
ModLength : 2048
Key ref : 0 (0x00)
Native : no
Path : a401
ID : 03
X.509 Certificate [Cardholder certificate]
Object Flags : [0x00]
Authority : no
Path : 3f007f21
ID : 03
Encoded serial : <serial>
The OpenPGP card's default admin PIN is 12345678 and the user pin 123456.
PKINIT Setup
Now add
[libdefaults]
pkinit_anchors = FILE:/etc/ssl/certs/ca.pem
to your /etc/krb5.conf and place the ca.pem in /etc/ssl/certs. With that you should be
able to use pkinit. The -C option tells kinit to use your smart card for the crypto:
$ kinit -C PKCS11:/usr/lib/aarch64-linux-gnu/pkcs11/onepin-opensc-pkcs11.so foo@MS20.NET
PIN code for L5 built-in SmartCard Reader 00 01 00 00:
After entering the pin and typing klist the output should be
similar to the klist output above. If you connect to various Kerberized services in your
realm (e.g. by sending mail) the list will grow without having to
retype any PINs or passwords:
$ klist
Credentials cache: FILE:/tmp/krb5cc_1000
Principal: foo@ms20.nix
Issued Expires Principal
Oct 24 12:55:13 2022 Oct 25 12:55:13 2022 krbtgt/MS20.NIX@MS20.NIX
Oct 24 12:55:57 2022 Oct 25 12:55:13 2022 imap/imap.ms20.nix@
Oct 24 12:57:45 2022 Oct 25 12:55:13 2022 smtp/smtp.ms20.nix@
Oct 24 13:00:32 2022 Oct 25 12:55:13 2022 HTTP/http.ms20.nix@
Can we make this simpler?
The above is very command line heavy and thus hard to use on a
phone. With krb5-auth-dialog things become easier to set
up. There's no need to adjust /etc//krb5.conf or to copy any
certificates. PKINIT via smartcard is being enabled by a single click
and you can select your CA (KDC trust anchor) via UI too:
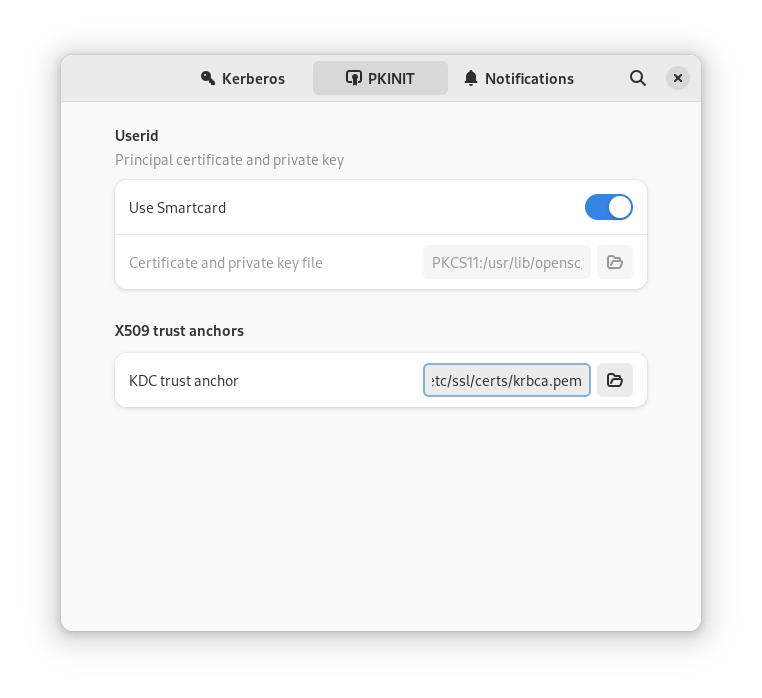
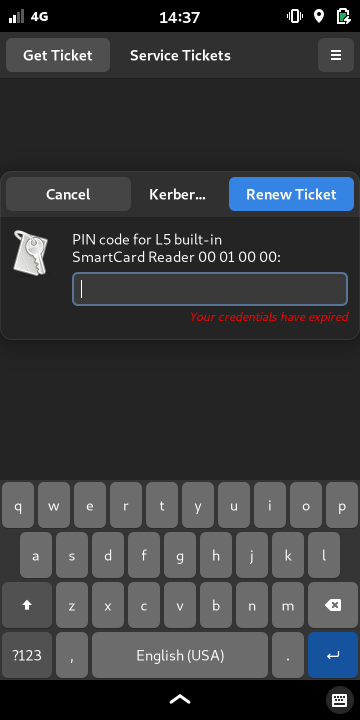
There's a graphical dialog to enter your PIN that can either be started via the menu or triggered via a simple DBus call:
$ gdbus call -e -d org.gnome.KrbAuthDialog -o /org/gnome/KrbAuthDialog -m org.gnome.KrbAuthDialog.acquireTgt ''
and the good part is that it won't prompt you if you already have a
valid ticket. So you can e.g. add this as a hook to your offlineimap
config.
As far as I know there's no end user friendly tool to transfer the certificates to the smartcard yet but note that this doesn't even have to happen on the phone itself. You can provision those elsewhere and then add the card to the phone but it might make sense to add that functionality to either krb5-auth-dialog or seahorse.
I hope this post motivates people to try this out and to leverage Kerberos for authenticating to services via the Librem 5's built-in smartcard reader.
Pitfalls
If you get errors like:
kinit: krb5_get_init_creds_opt_set_pkinit: Failed to init cert certs: Failed to init PKCS11 slot 0Then make sure
gpg-agentdidn't grab the card (e.g. because you rangpg --card-status).If Firefox won't authenticate to your server make sure you've set
negotiate.auth.trusted-urisin about:config
Since people are sometimes slightly surprised that you can go onto a multi week trip with a smartphone running free sofware so only I wanted to share some impressions from my recent trip to Prizren/Kosovo to attend Debconf 22 using a Librem 5. It's a mix of things that happend and bits that got improved to hopefully make things more fun to use. And, yes, there won't be any big surprises like being stranded without the ability to do phone calls in this read because there weren't and there shouldn't be.
After two online versions Debconf 22 (the annual Debian Conference) took place in Prizren / Kosovo this year and I sure wanted to go. Looking for options I settled for a train trip to Vienna, to meet there with friends and continue the trip via bus to Zagreb, then switching to a final 11h direct bus to Prizren.
When preparing for the trip and making sure my Librem 5 phone has all the needed documents I noticed that there will be quite some PDFs to show until I arrive in Kosovo: train ticket, bus ticket, hotel reservation, and so on. While that works by tapping unlocking the phone, opening the file browser, navigating to the folder with the PDFs and showing it via evince this looked like a lot of steps to repeat. Can't we have that information on the Phone Shell's lockscreen?
This was a good opportunity to see if the upcoming plugin infrastructure for the lock screen (initially meant to allow for a plugin to show upcoming events) was flexible enough, so I used some leisure time on the train to poke at this and just before I reached Vienna I was able to use it for the first time. It was the very last check of that ticket, it also was a bit of cheating since I didn't present the ticket on the phone itself but from phosh (the phones graphical shell) running on my laptop but still.
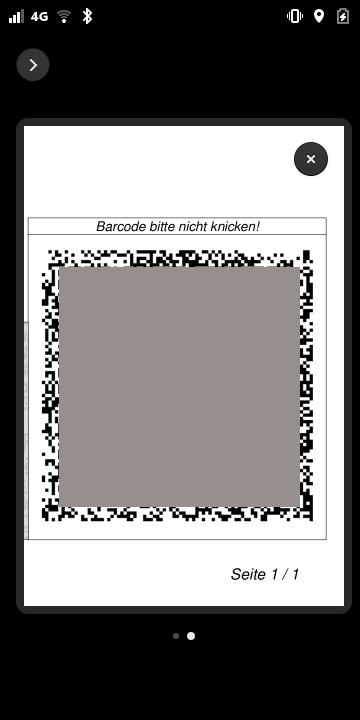
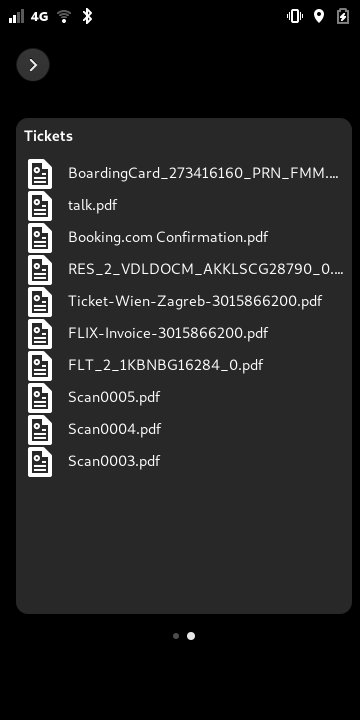
This was possible since phosh is written in GTK and so I could just leverage evince's EvView. Unfortunately the hotel check in didn't want to see any documents ☹.
For the next day I moved the code over to the Librem 5 and (being a bit nervous as the queue to get on the bus was quite long) could happily check into the Flixbus by presenting the barcode to the barcode reader via the Librem 5's lockscreen.
When switching to the bus to Prizren I didn't get to use that feature again as we bought the tickets at a counter but we got a nice krem banana after entering the bus - they're not filled with jelly, but krem - a real Kosovo must eat!).
Although it was a rather long trip we had frequent breaks and I'd certainly take the same route again. Here's a photo of Prizren taken on the Librem 5 without any additional postprocessing:

What about seeing the conference schedule on the phone? Confy(a conferences schedule viewer using GTK and libhandy) to the rescue:
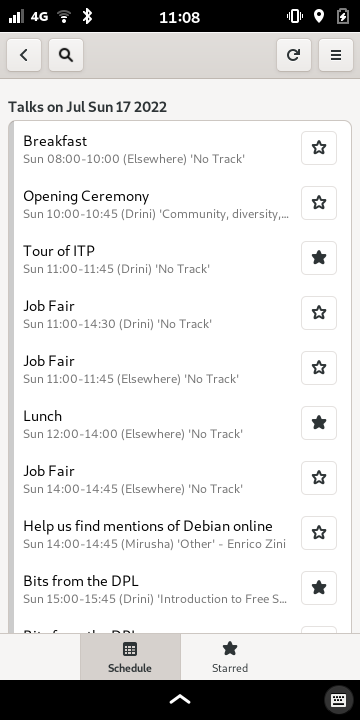
Since Debian's confy maintainer was around too, confy saw a bunch of improvements over the conference.
For getting around Puremaps(an application to display maps and show routing instructions) was very helpful, here geolocating me in Prizren via GPS:
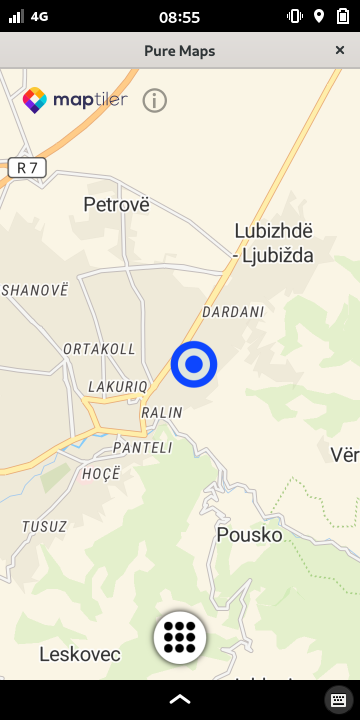
Puremaps currently isn't packaged in Debian but there's work onging to fix that (I used the flatpak for the moment).
We got ourselves sim cards for the local phone network. For some reason mine wouldn't work (other sim cards from the same operator worked in my phone but this one just wouldn't). So we went to the sim card shop and the guy there was perfectly able to operate the Librem 5 without further explanation (including making calls, sending USSD codes to query balance, …). The sim card problem turned out to be a problem on the operator side and after a couple of days they got it working.
We had nice, sunny weather about all the time. That made me switch between high contrast mode (to read things in bright sunlight) and normal mode (e.g. in conference rooms) on the phone quite often. Thankfully we have a ambient light sensor in the phone so we can make that automatic.

See here for a video.
Jathan kicked off a DebianOnMobile sprint during the conference where we were able to improve several aspects of mobile support in Debian and on Friday I had the chance to give a talk about the state of Debian on smartphones. pdf-presenter-console is a great tool for this as it can display the current slide together with additional notes. I needed some hacks to make it fit the phone screen but hopefully we figure out a way to have this by default.

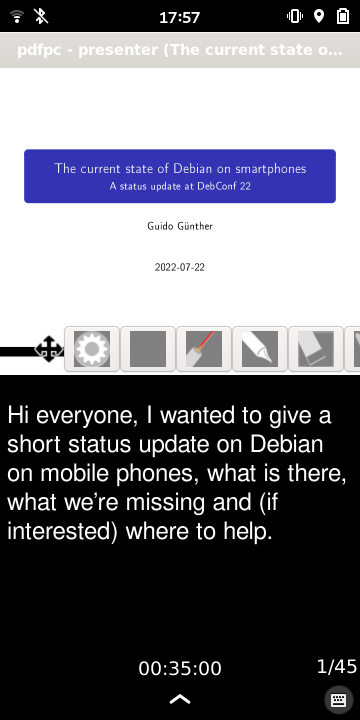
I had two great weeks in Prizren. Many thanks to the organizers of Debconf 22 - I really enjoyed the conference.
For a slightly more up to date version see here
phosh is graphical shell for mobile, touch based devices like smart phones. It's the default graphical shell on Purism's Librem 5 (and that's where it came to life) but projects like postmarketOS, Mobian and Debian have picked it up putting it into use on other devices as well and contributing patches.
This post is meant as a short overview how things are tied together so further posts can provide more details.
A PHone SHell
As mobile shell phosh provides the interface components commonly found on mobile devices to
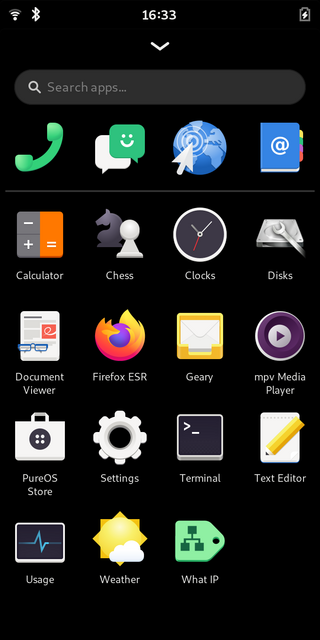
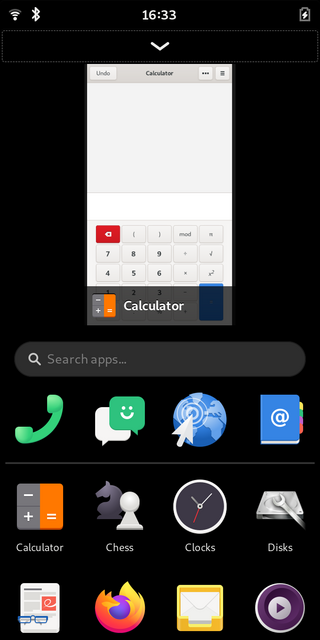
- launch applications
- switch between running applications and close them
- lock and unlock the screen
- display status information (e.g. network connectivity, battery level)
- provide quick access to things like torch or Bluetooth
- show notifications
It uses GObject object system and GTK to build up the user interface components. Mobile specific patterns are brought in via libhandy.
Since phosh is meant to blend into GNOME as seamlessly as possible it
uses the common interfaces present there via
D-Bus like
org.gnome.Screensaver or org.gnome.keyring.SystemPrompter and
retrieves user configuration like keybindings via
GSettings from preexisting
schema.
The components of a running graphical session roughly look like this:
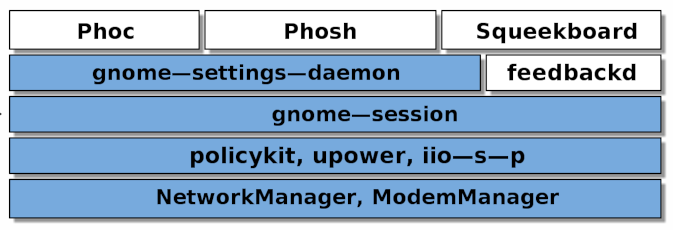
The blue boxes are the very same found on GNOME desktop sessions while the white ones are currently only found on phones.
feedbackd is explained quickly: It's used for providing haptic or visual user feedback and makes your phone rumble and blink when applications (or the shell) want to notify the user about certain events like incoming phone calls or new messages. What about phoc and squeekboard?
phoc and squeekboard
Although some stacks combine the graphical shell with the display server (the component responsible for drawing applications and handling user input) this isn't the case for phosh. phosh relies on a Wayland compositor to be present for that. Keeping shell and compositor apart has some advantages like being able to restart the shell without affecting other applications but also adds the need for some additional communication between compositor and shell. This additional communication is implemented via Wayland protocols. The Wayland compositor used with phosh is called phoc for PHone Compositor.
One of these additional protocols is wlr-layer-shell. It allows the shell to reserve space on the screen that is not used by other applications and allows it to draw things like the top and bottom bar or lock screen. Other protocols used by phosh (and hence implemented by phoc) are wlr-output-management to get information on and control properties of monitors or wlr-foreign-toplevel-management to get information about other windows on the display. The later is used to allow to switch between running applications.
However these (and other) Wayland protocols are not implemented in phoc from scratch. phoc leverages the wlroots library for that. The library also handles many other compositor parts like interacting with the video and input hardware.
The details on how phoc actually puts things up on the screen deserves a separate post. For the moment it's sufficient to note that phosh requires a Wayland compositor like phoc.
We've not talked about entering text without a physical keyboard yet - phosh itself does not handle that either. squeekboard is the on screen keyboard for text (and emoji) input. It again uses Wayland protocols to talk to the Wayland compositor and it's (like phosh) a component that wants exclusive access to some areas of the screen (where the keyboard is drawn) and hence leverages the layer-shell protocol. Very roughly speaking it turns touch input in that area into text and sends that back to the compositor that then passes it back to the application that currently gets the text input. squeekboard's main author dcz has some more details here.
The session
So how does the graphical session in the picture above come into existence? As this is meant to be close to a regular GNOME session it's done via gnome-session that is invoked somewhat like:
phoc -E 'gnome-session --session=phosh'
So the compositor phoc is started up, launches gnome-session which then looks at phosh.session for the session's components. These are phosh, squeekboard and gnome-settings-daemon. These then either connect to already running services via D-Bus (e.g. NetworkManager, ModemManager, ...) or spawn them via D-Bus activation when required (e.g. feedbackd).
Calling conventions
So when talking about phosh it's good to keep several things apart:
- phosh - the graphical shell
- phoc - the compositor
- squeekboard - the on screen keyboard
- phosh.session: The session that ties these and GNOME together
On top of that people sometimes refer to 'Phosh' as the software collection consisting of the above plus more components from GNOME (Settings, Contacs, Clocks, Weather, Evince, ...) and components that currently aren't part of GNOME but adapt to small screen sizes, use the same technologies and are needed to make a phone fun to use e.g. Geary for email, Calls for making phone calls and Chats for SMS handling.
Since just overloading the term Phosh is confusing GNOME/Phosh Mobile Environment or Phosh Mobile Environment have been used to describe the above collection of software and I've contacted GNOME on how to name this properly, to not infringe on the GNOME trademark but also give proper credit and hopefully being able to move things upstream that can live upstream.
That's it for a start. phosh's development documentation can be browsed here but is also available in the source code.
Besides the projects mentioned above credits go to Purism for allowing me and others to work on the above and other parts related to moving Free Software on mobile Linux forward.